Services/ Security
Security
Modern Security Solutions for Cloud & Infrastructure

Security
Modern Security Solutions for Cloud & Infrastructure
Services/ Security
Cyber threats are evolving rapidly, making it essential to strengthen cloud and infrastructure security. Celebal Technologies delivers advanced protection with Microsoft’s security suite, ensuring continuous threat detection and rapid response. Our approach safeguards identities, endpoints, and data while addressing compliance requirements. By integrating intelligent monitoring and automated risk mitigation, we help enterprises stay resilient against cyber risks. With expert-driven strategies, we enable secure operations without disruption.
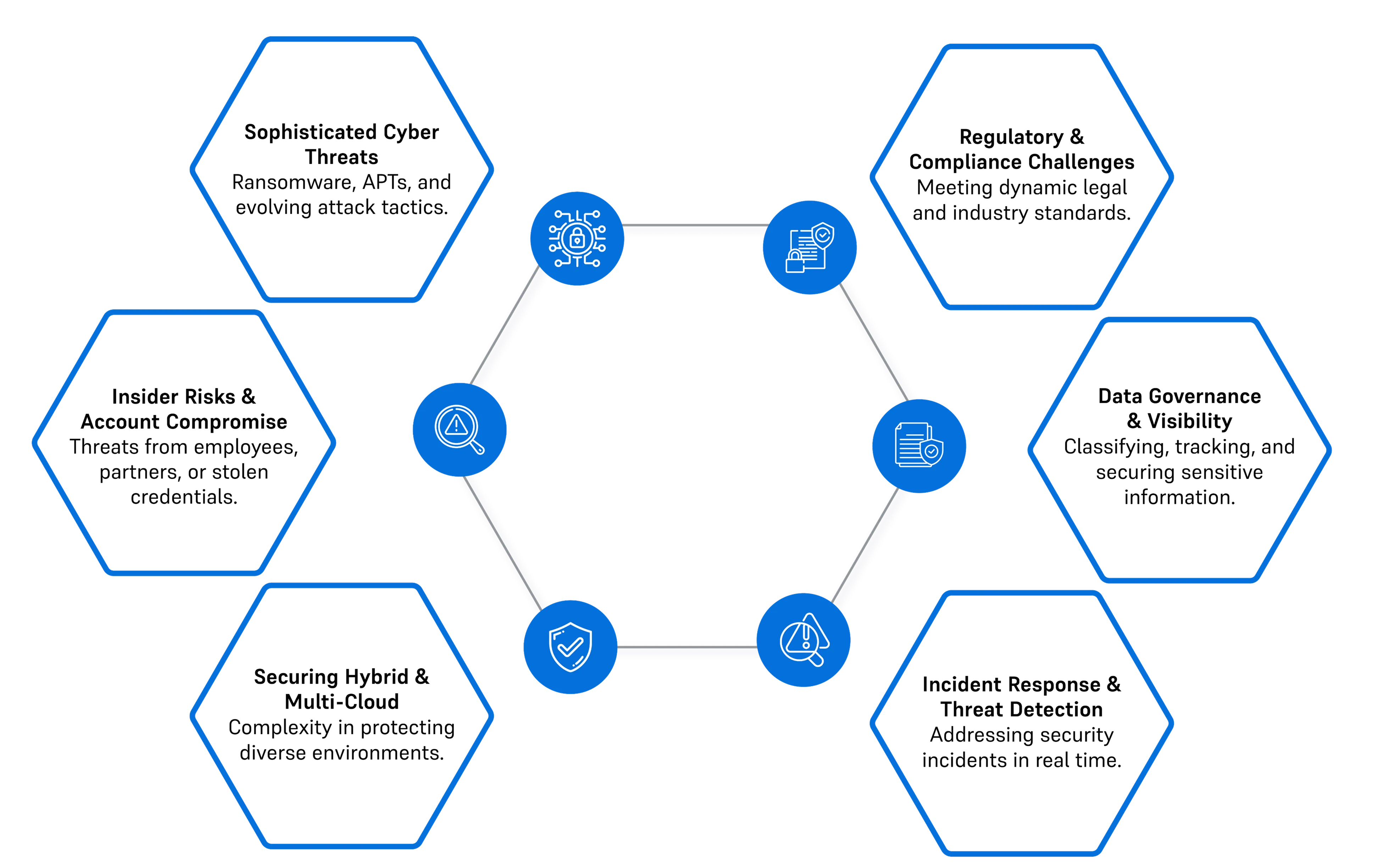
Key Security Challenges in Cloud & Infrastructure
Fortifying Security with Our Expertise
Impact
Oil & Gas and Mining
Power Utilities
Renewables
Sustainability
Manufacturing
Retail & CPG
BFSI
ITES
Healthcare & Life Sciences
Communication, Media & Entertainment (CME)
How We Are Strengthening Enterprise Security Solutions?
Defender
Proactive Threat Protection
Celebal Technologies enhances security by integrating AI-driven threat intelligence, enabling early detection and swift mitigation of cyber threats.
Tailored Security Implementation
We adapt Defender’s capabilities to meet enterprise-specific security needs, strengthening protection across endpoints, identities, and cloud environments.
Automated Response & Remediation
Leveraging automation, we streamline incident response, reducing downtime and minimizing security risks.
Security Insights & Analytics
Our expertise in data analytics provides deeper visibility into security events, helping enterprises make informed decisions.
Success Stories
Secure Modernization with M365
Client Overview
A leading enterprise sought to enhance its security framework by implementing advanced information protection and data loss prevention measures. With a newly appointed Security Manager, the client required a structured setup for Microsoft 365 E5 Information Protection to secure sensitive data.
Business Challenge
Understanding and configuring M365 security capabilities
Implementing a structured setup for Information Protection using MIP and DLP
Ensuring seamless application of security labels and policies
Approach
To streamline information security, our experts executed a tailored deployment by identifying and classifying sensitive data using predefined labels and policies for Information Protection, while implementing Data Loss Prevention (DLP) policies to regulate and safeguard data exchange across internal and external environments.
Outcomes
Enhanced Security Posture – Strengthened data security with automated protection measures. Seamless Implementation – Efficiently deployed MIP and DLP while integrating Active Directory Premium for identity protection. Optimized Decision-Making – Provided actionable recommendations, enabling the client to make informed security investments.

Ready to modernize and secure your IT infrastructure
Deploy advanced protection with Celebal Technologies' security solutions.